If you’re serious about “becoming your own bank” and taking self custody of your money, you must keep security top of mind.
You don’t need to be extremely technical.
However, you must be aware that there are many elite and persistent hackers who are committed to stealing your funds.
Fortunately, you don’t have to be an expert to greatly reduce your risk.
In this article I will:
Explain the necessary security mindsets
Give you essential tips to improve your security posture
Cover the critical concepts that will help you understand why the practical tips are what they are
The third point is the most important. If you parrot tips like “use a hardware wallet” without understanding what a hardware wallet is or does then it may be totally useless to you. Don’t expect to deeply understand every concept overnight, but make sure that you do understand everything in this article if you have significant funds onchain.
There may be words in this article you don’t understand. That’s fine, they’ll all be explained. Treat the tips as a checklist. Are you doing every tip? Do you understand why it’s important? If not, look out for the concept(s) that apply to it in the following sections.
There will be a part 2 which covers other essential topics such as: transaction types, how to never sign a malicious transaction, smart contract risks, and common attack vectors. For now, part 1 will give you a strong foundation.
Note that this article covers security not privacy.
Security is protection against threats. Privacy is your right to control how your information is viewed or used. By improving and understanding your security posture you will likely also increase your onchain privacy, but they separate.
Lets rock.
Security Mindset
Slow is smooth, smooth is fast
Defenders must be win every time. Attackers only have to be successful once. Every day you are playing to not lose.
Tips:
Avoid self custody until you are confident
Go through a checklist before making high value transactions
Never make transactions while in a rush
Never make transactions while sleep deprived or intoxicated
Make test transactions before sending large amounts
Defense in Depth
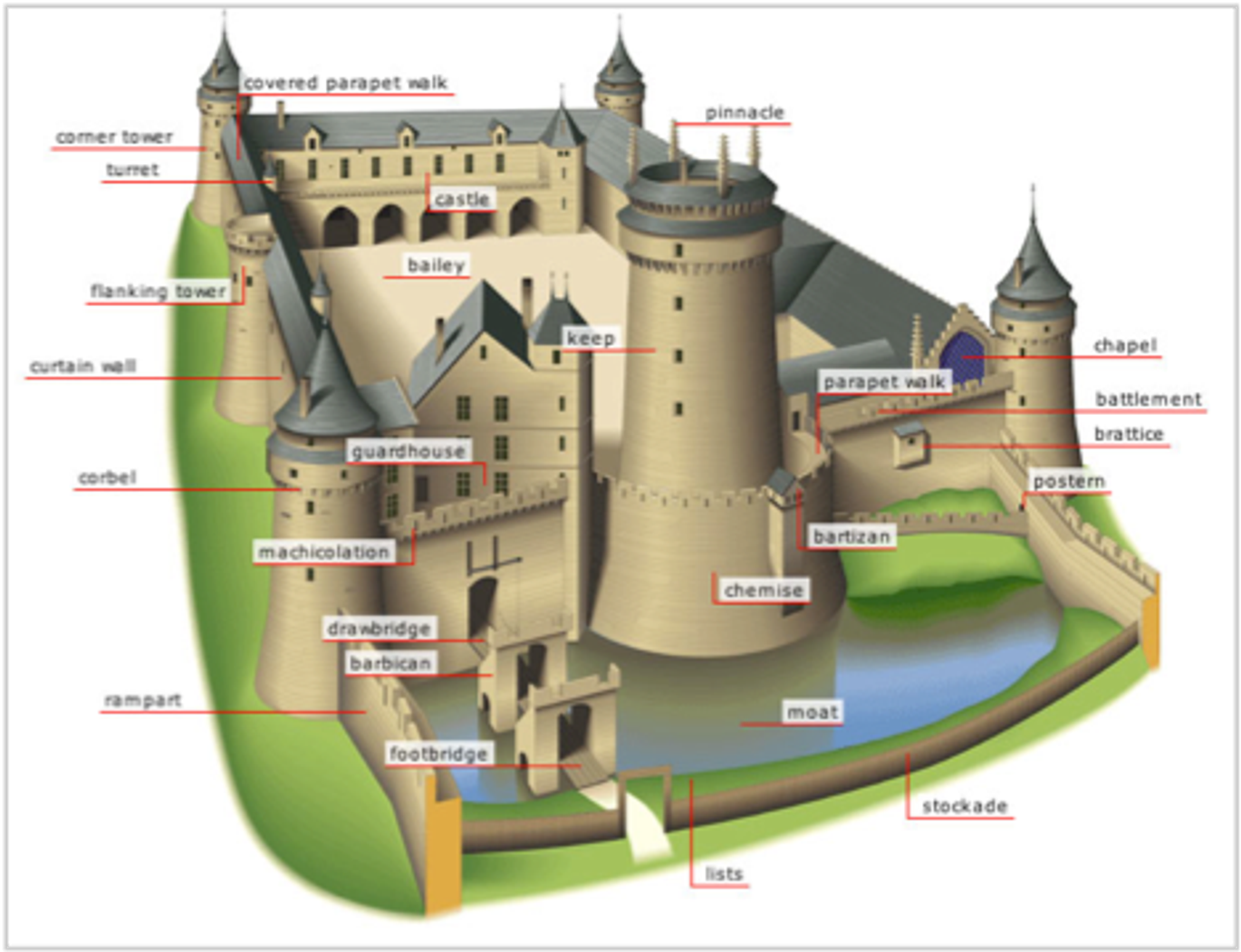
Imagine a castle’s defenses.
A stockade, moat, turrets, walls, towers, a defensible keep, etc. It’s not all over even if the walls are breached.
You should treat your digital asset custody like this castle, taking multiple measures to ensure security. Hope nothing happens, but plan for your assets to still be safe even if something goes wrong.
Tips:
Don’t rely on one seed phrase alone
Don’t rely on one hardware device alone
Check every transaction
Separate funds into several addresses
Don’t keep important crypto keys on work, personal, or dev machines
Bookmark commonly used crypto sites
Use burner wallets
Keep a metallic backup of your important seed phrases
Revoke Approvals regularly
Cycle wallets regularly
Use multisig wallets for large amounts you don’t move frequently
Use a unique email for all financial apps (like CEXs)
Use unique passwords for every website and app
Use 2FA wherever possible, avoid SMS 2FA always
Isolate risk
While defense in depth involves multiple layers of defense for your “castle”, isolating your risk is like spreading your assets to multiple castles.
This reduces your downside risk in the event you have a security breach, and also can help reduce “security fatigue”.
“Security Fatigue” = mental exhaustion and reluctancy to maintain proper security hygiene due to constant bombardment of security demands, warnings, and tasks.
Convenience and security are inversely related.
The more secure something is, often the less easy and convenient. If it was as difficult to collect a POAP as it was to access your HODL stack of BTC then that would get old real fast.
If you are not maintaining proper security habits, it’s likely due to security fatigue. Instead of feeling guilty, acknowledge this phenomenon and plan accordingly.
For low value engagements, high security standards may not be a priority. Knowing when to maximize security and when to lean towards convenience reduces security fatigue and makes using low-stakes onchain apps stress free.
Not every castle needs to be maximum security.
If you’re trying a new onchain social game, maybe you can keep lower security standards. Securing millions of dollars of BTC would demand higher security standards. It’s critical to have tiered security standards for different environments and to not mix those environments.
By isolating your risk and practicing controlled separation of concerns you can minimize your security fatigue and maintain high security standards where it matters.
Tips:
Have multiple seed phrases
Have many public addresses
Practice tiered security standards for different addresses and wallet environments
Use a dedicated computer for your “maximum security” environment
Use “Vault” address(es) that have no smart contract approvals
Maintain strict security standards and practices when operating in your high security environment
Use burner addresses and wallets for interacting with new or less trusted contracts
Use different browser profiles for different software wallets.
If a seed phrase is in a software wallet do not have any other extensions downloaded in that web browser profile.
Now, lets apply these mindsets of “slow is smooth, smooth is fast”, “defense in depth”, and “isolating risk”.
Offchain Security
“Offchain” refers to everything that is not on the blockchain or interacting with the blockchain.
Centralized Exchange (CEX) Security
Securing your CEX is similar to securing any other online financial service like a bank or brokerage account.
For maximum security you should be using a unique email, or at least one that is private and has no history of being leaked.
If someone is trying to access your CEX, they are going to try emails that are linked to you. They will try email/password combos that have previously been involved in data breaches. The most straight forward defense is to use an email and password that have never been used anywhere else.
You can check if your email has been a part of a data breach here.
The next step is always keeping 2FA enabled. Ranking 2FA in order from best to worst:
Hardware key
TOTP (Apps like Microsoft Authenticator or Google Authenticator are examples, but there are other open source alternatives)
SMS
Avoid using SMS 2FA. In many cases it can be less secure than not using 2FA at all. Make sure you are not using SMS 2FA for your email, especially emails securing financial accounts.
The last essential step for max CEX security is requiring an allowlist or time delayed withdrawals.
An allowlist means you can only withdraw to addresses on that list. You can add to the list, but it will send an email notification and there will be a time delay. So, if an attacker gets in and tries to send funds to their address you have time to see, contact the CEX, and stop the withdrawal from ever occurring.
In Summary:
Unique email & password
2FA
Address allowlisting and/or time delays on withdrawal
Seed Phrase & Private Key Security
Important Terminology:
The act of isolating a device, network, or piece of data from other devices or networks
Seed Phrase (aka mnemonic):
A sequence of words that serves as a backup for your master private key
Wallet (aka wallet software):
A piece of software that allows you to sign transactions and interact with blockchain apps (dApps). Most wallets have the ability to store your seed phrase, but that is always less secure since the software wallet itself is not air gapped.
Software wallets are generally compatible with most popular hardware wallets.
Software wallets are generally interchangeable. You can use your hardware wallet or seed phrase with many different software wallets.
Your funds are not stored in the wallet software. They are instead represented on the blockchain ledger (more on that later).
Examples: Metamask, Rabby, Phantom
Software Wallet:
Similar to a “wallet” or “wallet software”. Typically, when people say “software wallet” they are referring to using their wallet software without the use of a hardware wallet.
This explains why people will say “don’t use software wallets, always use a hardware wallet”. Typically, everyone has to use some sort of wallet software, but you want to isolate your seed phrase from that wallet software. To do that you would use a hardware wallet. When not doing that, the setup is typically referred to as a “software wallet”.
Hardware Wallet:
A physical device used to store your seed phrase air gapped away from your wallet software, computer, or device.
Some hardware wallet manufacturers also have their own wallet software (ex. ledger live). However, most popular wallet software support most popular hardware wallets and vice versa.
Master private key:
Similar to your seed phrase, but not a series of words. It’s basically how a machine reads your seed phrase. I will often use the terms “seed phrase”, “mnemonic”, “mnemonic seed phrase”, and “master private key” interchangeably.
Since a master private key is very difficult for a human to correctly write down and remember, we typically use seed phrases instead. Just know that the hardware wallet or software wallet is able to derive the master private key from the seed phrase.
Some of the most common exploits are due to compromised seed phrases.
To protect your seed phrase, generate it on an air gapped device (HW), write it down physically on a piece of paper and/or engrave it in metal, and do not ever share it or store it digitally. If that seed phrase is compromised then every address controlled by it is compromised (more on that later).
If a seed phrase or private key is ever exposed to any internet connected device then it can no longer be considered air gapped. Don’t take pictures of it, don’t store it in a text file on your computer, don’t put it in a password manager, and certainly don’t put it into any wallet software.
If your seed phrase was generated or input into a software wallet ever at any time, then the “air gap seal” has been broken. It is no longer a maximum security seed phrase. Which means in order to maintain the highest possible security standards it must be deprecated (aka retired). It could still be used for lower security use cases.
Your seed phrase must be kept secret. I’ll repeat, if the seed phrase is compromised, every address it controls is compromised.
Onchain Security Pt. 1
Address Separation
Yes, you read “every address.”
Your “public address” is like a mailbox people can send funds to. If you send tokens to someone else, they’ll see it as your public address sending the tokens. If you deposit crypto to an exchange, they’ll give you a public address to send it to. When you withdraw, they’ll ask for a public address from you so they know where to send it.
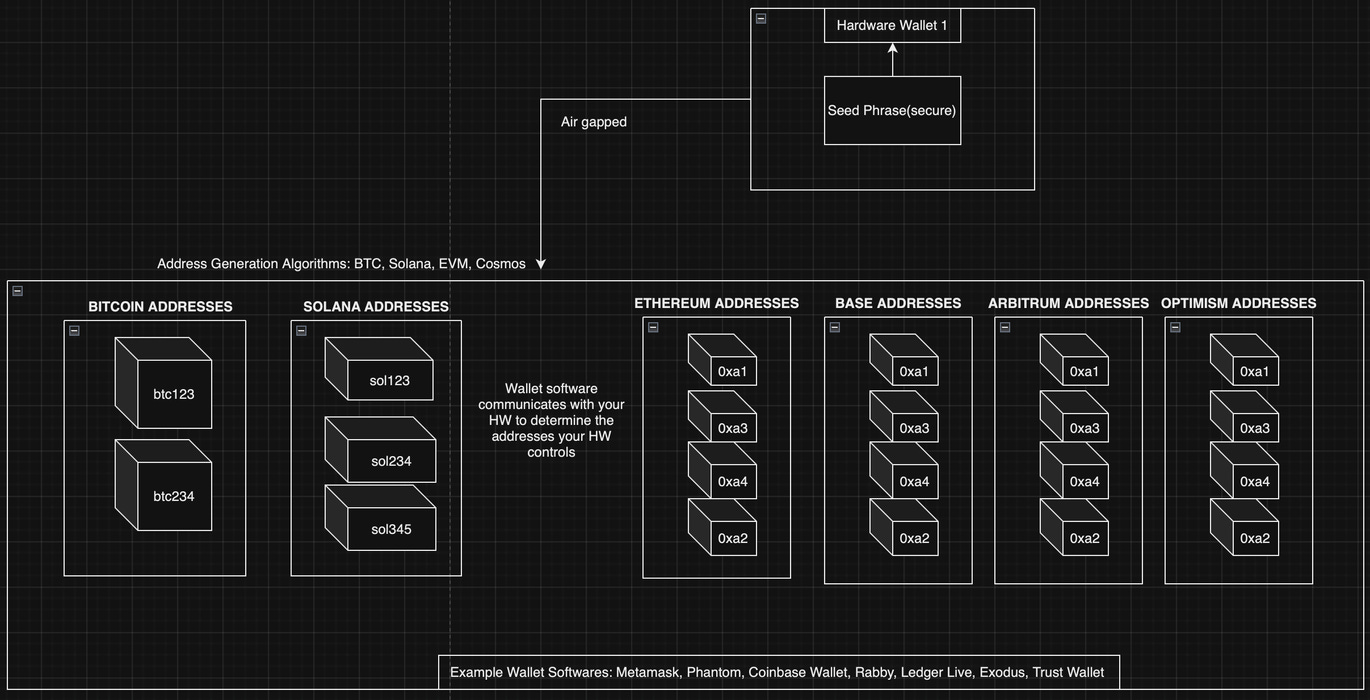
Each seed phrase controls many public addresses.
That master private key basically “has” tons and tons of child private keys. Each of those child private keys maps to a public key. Chop the first 20-60 digits (depending on the blockchain) off of those public keys and you’ve got your public addresses.
That’s true for Bitcoin, Solana, and all EVM chains uniquely.
The logic goes like:
Seed phrase → one master private key → many child private keys → many addresses
Different blockchains have different standards for turning those “child private keys” into their respective public keys and turning those public keys into addresses.
The good news is that all the EVM chains (Ethereum, Base, Arbitrum, Polygon, basically all L2s, BSC, etc) do it the same way.
That’s why when you go to Solana, Bitcoin, or Ethereum with the same “hardware wallet” (aka seed phrase) you see totally different addresses. When you go to Ethereum and bridge over to Base you see the same address. Both Base and Ethereum are build with similar technology and basically use the same algorithm for turning private keys into public addresses.
Each public addresses on each blockchain has different data “in” it.
The most important data to you might be how much ETH or USDC you have, but there is other data as well like token approvals, smart contract interactions, etc.
As you can see, one seed phrase might control hundreds of active addresses across dozens of blockchains.
Each box represents a different public address. You can use your wallet software to switch between each. You can isolate your risk and have different security standards for each public address.
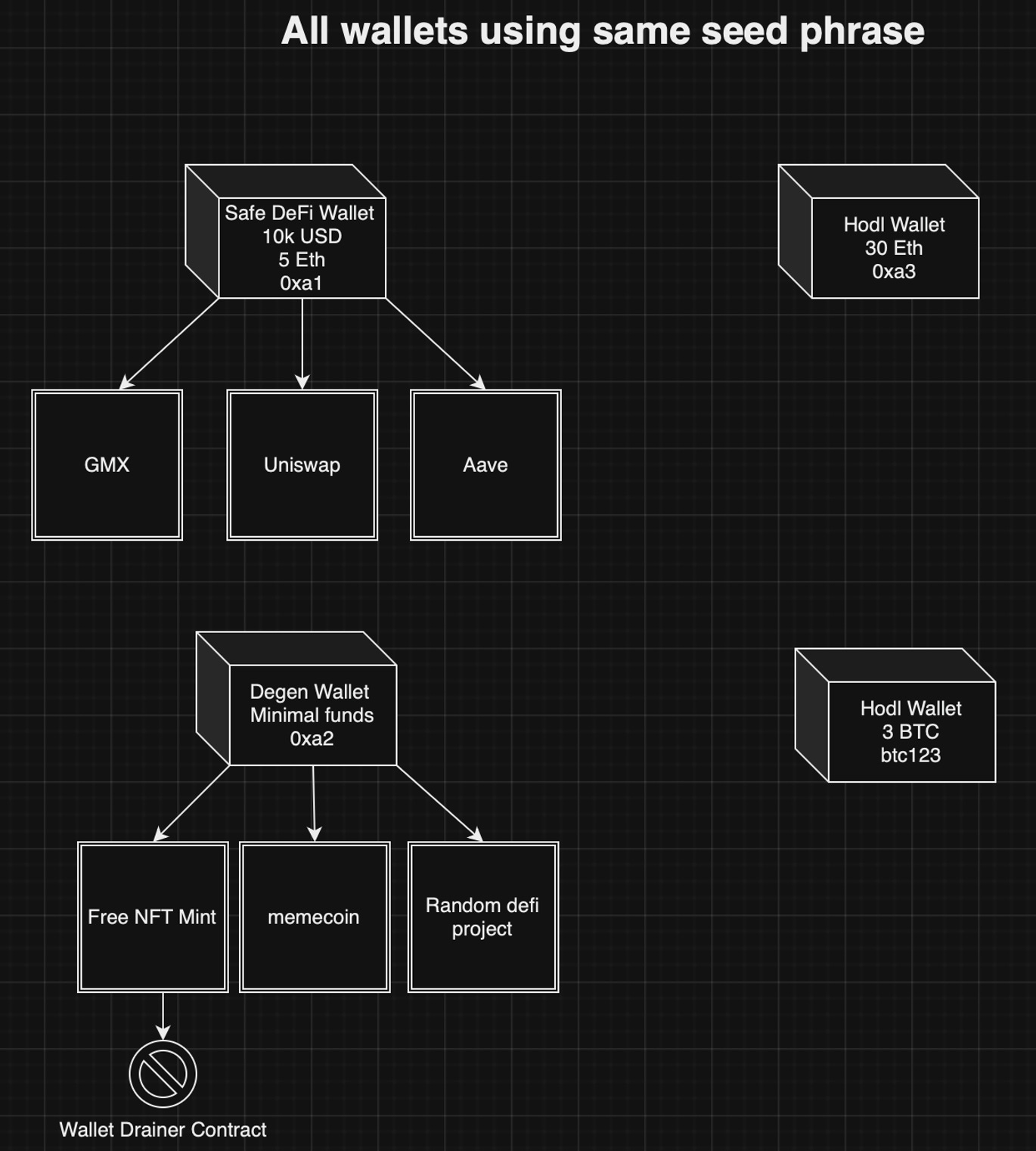
If we zoom in on the activity, we can see that in address 0xa1 you could be using more established DeFi projects, in 0xa3 holding spot ETH with no smart contract interactions, in 0xa2 be getting all your assets drained, and in btc123 holding spot BTC. All of this can occur while using 1 hardware wallet with just 1 seed phrase in it.
Of course, if 30 ETH and 3 BTC is significant for you, it would be best practice to isolate that from degen activities even further. Perhaps by using a different hardware wallet, different seed phrase, and a separate computer that is dedicated to max security transactions.
After a while, you may just want a clean slate.
Maybe you want to improve your privacy by wiping your transaction history or you want to eliminate all smart contract approvals without going through them one by one. In that case you can just send all the assets in one address (0xa2) to a brand new address (0xa4).
Boom, just like that you’ve moved your funds from an address with a history of interacting with a malicious smart contract to a totally fresh address with zero smart contract approvals. This is called “address cycling” or “wallet cycling” and should be a regular practice for addresses that have a lot of smart contract activity.
Address separation is customizable to fit your exposure and risk tolerance. It’s critical when practicing our “Defense in Depth” and “Isolate risk” mindsets.
Securing your digital assets requires vigilance, layered defenses, and compartmentalizing risk. By being thoughtful about your approach to security, you can protect yourself even with limited technical knowledge .
Security is an ongoing practice, start with the essentials outlined here, and stay tuned for part 2 where we’ll expand on onchain security.
Good Reads
I highly recommend both Cyfrin’s Web3 Wallet Security Basics & Advanced courses. They contain all the critical skills required to never sign a malicious transaction.
Disclaimer: None of this is to be deemed legal or financial advice of any kind. These are the *opinions* of a guy on the internet with a DeFi and IT Security background.
Need help? Reply to this email with your questions.